
| Menu | |
|
: Home |
|
| Search | |
|
|
![]()
![]()
Security Domains
Introduction
This brief document aims to clarify the term security domain. Section 2 lists definitions collected from security related documents. Section 3 relates the terminology to the differentiated security model.
Definitions
Below are definitions and descriptions cited from security standards and other relevant documents.
- A collection of users and systems subject to a common security policy [5].
- A security domain (domain) is defined as a (sub)system under the control of a single authority which the entities therein trust. The security policy in place over a domain is defined either implicitly or explicitly by its authority [4].
- A security domain is typically the set of processing and communications resources belonging to one organisation [2].
- A security domain is a single domain of trust that shares a single security policy and a single management. Historically, security domains have been used to define a single system. Modern networks often implement security domains that include many systems [5].
- The term 'security domain' as used in RFC 3183 is defined as a collection of hardware and personnel operating under a single security authority and performing a common business function. Members of a security domain will of necessity share a high degree of mutual trust, due to their shared aims and objectives.
A security domain is typically protected from direct outside attack by physical measures and from indirect (electronic) attack by a combination of firewalls and guards at network boundaries. The interface between two security domains is termed a 'security boundary'. One example of a security domain is an organizational network ('Intranet')[1].
It is clear from looking at the very limited number of definitions reproduced above that security domain can be used and applied to whatever constitutes a domain in any given context.
Discussion
The straight forward definition of a security domain is a domain subject to a common security policy. It is possible to define domains such that they are detached from the infrastructure they are using for communication etc., as well as from strict organisational boundaries. In today’s complex network environments it is likely that security policies, for example, will need to be defined for applications or groups of applications that neither conforms to a single ‘network domain’ or ‘owner domain’.
A domain can, for example, be defined to include an application or a group of applications. However, since security domains often are assumed to have either physical/technical or organisational boundaries it might be useful to find a different term when different kinds of domains are addressed.
Meta-group uses the term trust domain to describe a domain which can be made up from resources belonging to different security domains. A trust domain is (as it appears) related to applications in their model. A complete application can be made up of components located on different networks (and security domains), as illustrated in figure 1. Applications can be very complex and made up of many subsystems as well as having users spread out over several security domains.
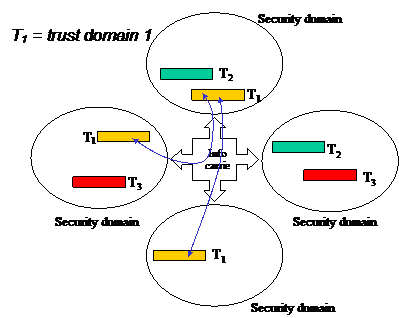
Figure 1 – Illustrating how a trust domain can be made up of
components from several security domains [3]
By applying the differentiated security model and its security classification scheme to the various sub-systems, or modules, a complete application can be built, where the application can be classified according to the lowest level of the constituent sub-systems. This application (or system) corresponds to a trust domain in the Meta-group model. If the individual sub-systems comply with a certain (minimal) security level and no sub-system or link (including their interfaces) are classified below this level, the complete system can also be classified to this level.
References
- [1] T. Dean and W. Ottaway, Domain Security Services using S/MIME, IETF RFC 3183, October 2001
- [2] Warwick Ford, Computer Communication Security: Principles, Standard Protocols and Techniques, Prentice Hall, 1993.
- [3] ISO/IEC 15816: 2002 (ITU-T X.841), Security information objects for access control, 2002.
- [4] Menezes, P. van Oorschot, and S. Vanstone. Handbook of Applied Cryptography. Discrete Mathematics and Its Applications. CRC Press, 1996.
- [5] Hal Tipton and Micki Krause, Handbook of Information Security Management, CRC Press LLC, 1998.
Links
| Copyright 2006-2008. All Rights Reserved. | Something missing on this page? Let us know |